Home LAN
17 May 2025 · Network

Overview
The cabling isn't mine, it's the back of one of the racks in the lab at work, I wish my cabling was the tidy... maybe one day!
I'm not an engineer. I do like dabbling with stuff, so this is a bit dabbly and I'm sure there's a better way to do what I want to do, but this works for me, so I'm good with it.
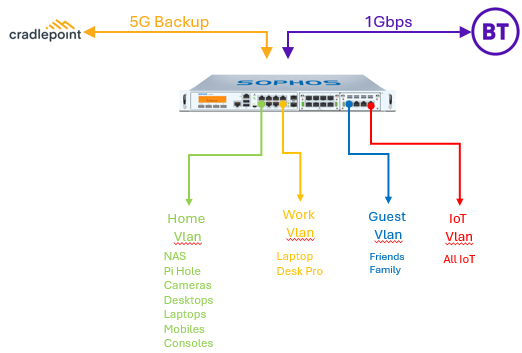
I've got some devices which I look after and trust, desktops, laptops, mobile devices, cameras etc. Some devices which I look after and don't trust, Alexas, WiFi plugs, temp sensors, Hive etc. My work laptop which I don't manage or trust, but I know it's good, it's not an IoT device! We have friends / family over who bring their own (untrusted) devices. I wanted to keep everything seperated to minimise cross contamination!
Everything I trust goes in the Home VLAN, everything has access to the NAS, everyone has a user account, their own storage pool on the NAS, access to the printer, can use internal DNS to reach other things, has advert blocking and firewall rules based on user account.
Everything I don't trust and is mine goes in the IoT VLAN - access to the internet, but no access to internal resources.
Friends & Family use the Guest VLAN - there's a 3D printed QR code to make connecting nice and easy. They have access to the internet with some firewall rules stopping dodgy browsing. No access to internal resources.
My work laptop sits in the Work VLAN - straight out to the internet, with no access to internal resources. We use zScaler for remote access at work and it doesn't play nice with my network.
Design
Design is probably a bit grand! Like I say, it works, so it's all good in my eyes.
- 10.x.x.x addressing with reserved ranges per VLAN
- Pi-hole upstream to UTM; UTM to ISP
- 1Gbps primary internet & 5G backup
- Synology Directory Server for account privileges
- Synology NAS for central file storage & a few other services
- Shared printer & scanner
